I just found this while glancing through my news feed on GitHub. Built by Stephen LaPorte and Mahmoud Hashemi, this is a very abstract and relaxing visualisation of all the different edits on Wikipedia. It’s actually really nice to just listen to, especially when new users register occasionally!
In 2008, two Wikipedia administrators (PeterSymonds and Chet B Long) allowed another user (Steve Crossin) to access their administrator accounts. As expected, this was eventually discovered and trout was used extensively across the board. While those users have learnt their lesson, and a lot more users learnt from their mistake too, it seems not everyone learnt that lesson or studied history to learn from that.
A couple of weeks ago, two high-profile users were uncovered to have done a similar deed – Riley Huntley asked Gwickwire to make an edit from his account while he was unable to do so. While Riley didn’t have administrator permissions on enwiki, he did on Wikidata, and thanks to the Single-User Login system that the WMF wikis use, this would have logged Gwickwire onto Riley’s Wikidata account at the same time.
- History: Peter, Chet, and Steve: Read section in the Administrators’ Noticeboard archives
- Now: Riley and Gwickwire: Read on AN/I
Aftermath
A fair few people who have been around a long time on Wikipedia have rolled their eyes, having seen this happen before and the results it took. GWickwire and Riley have both left, which I feel is an over-reaction, especially since Peter and Chet both only lost their administrator privileges, and only then for 5 months or so – and Peter is now a steward. Yes, it was a mistake, a foolish thing to do (especially given history), but it was 5 years ago so it was a decent amount of time ago. I think both Riley and GWickwire will probably come back at some point, but under different names.
This whole thing is a shame, cos Wikipedia has lost two good editors, who were good at what they did. ACC and #wikipedia-en-help have suffered a bit with their loss.
Linode have been amazing as usual, and recently increased network capacity (bandwidth increased 1000%), and doubled CPU capacity (from 4-core to 8-core), and in the last few days they’ve doubled the RAM in each plan! This is all part of their free* upgrades that happen every now and again.
(* They’ve also adjusted the pricing plans to be easier and more friendly. Thus, their (for example) $19.95 plan has been increased to $20. Technically, it’s not free, but for 5 cents?)
The migrations to the new systems take a while – but I’m planning to do it in the middle of the night. Downtime could be a couple of hours. The bonus is with this reboot, the capacity of the entire cluster will be doubled. :o
In other news, I’m planning on retiring pikachu, it’s caused me nothing but trouble with it’s disk arrays, and the lag from Roubaix compared to the Linodes in London has been less than desirable. Plus, with the new capacity that the London cluster has, there’s no real advantage to having a dedicated machine out in Roubaix (apart from the BOINC work that it’s been sat doing cos it could).
If you’re interested in trying out Linode, they do a free trial! Just please mention this referral code: c88742a23087c8758c2824221626a8c1226c1736
I’ve just found the solution to an issue which has been annoying me for months.
A bit of background – if you link to Nagios, you either link to the entire tool with it’s sidebar and main page, or you link to a specific page within it, losing the sidebar. Nagios includes a nice URL parameter which allows you to specify what the “main page” is, such as the service status view:
http://localhost/nagios/?corewindow=cgi-bin/status.cgi
However, if you try and click on any of the filters, such as “All Problems”, you end up getting an empty list.
It seems that the solution to this is to simply append the value ?host=all to the corewindow parameter:
http://localhost/nagios/?corewindow=cgi-bin/status.cgi%3Fhost=all
This makes it behave as expected. :)
As part of my analysis of the DNS protocol (I’m writing a DNS server from the ground up), I’ve learnt some cool things that the DNS protocol does to reduce the number of bytes transmitted over the wire.
Let’s say you do a DNS lookup for:
stwalkerster.co.uk. IN AAAA
The actual DNS data received as a response is something like this:
Transaction ID: 0x707c
Flags: 0x0100 Standard query response, No error
1... .... .... .... = Response: Message is a response
.000 0... .... .... = Opcode: Standard query (0)
.... .0.. .... .... = Authoritative: Server is not an authority for domain
.... ..0. .... .... = Truncated: Message is not truncated
.... ...1 .... .... = Recursion desired: Do query recursively
.... .... 1... .... = Recursion available: Server can do recursive queries
.... .... .0.. .... = Z: reserved (0)
.... .... ..0. .... = Answer authenticated: Answer/authority portion was not authenticated
.... .... ...0 .... = Non-authenticated data: Unacceptable
.... .... .... 0000 = Reply code: No error (0)
Questions: 1
Answer RRs: 1
Authority RRs: 0
Additional RRs: 0
Queries
stwalkerster.co.uk: type AAAA, class IN
Name: stwalkerster.co.uk
Type: AAAA (IPv6 address)
Class: IN (0x0001)
Answers
stwalkerster.co.uk: type AAAA, class IN, addr 2a01:7e00::f03c:91ff:feae:5fd9
Name: stwalkerster.co.uk
Type: AAAA (IPv6 address)
Class: IN (0x0001)
Time to live: 1 hour
Data length: 16
Addr: 2a01:7e00::f03c:91ff:feae:5fd9
… or at least, that’s a marked-up representation the actual byte stream. The actual byte stream looks like this (Ethernet/IP/UDP headers hidden for clarity):
0000 .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. ................ 0010 .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. .. ................ 0020 .. .. .. .. .. .. .. .. .. .. 70 7c 81 80 00 01 ..........p|.... 0030 00 01 00 00 00 00 0c 73 74 77 61 6c 6b 65 72 73 .......stwalkers 0040 74 65 72 02 63 6f 02 75 6b 00 00 1c 00 01 c0 0c ter.co.uk....... 0050 00 1c 00 01 00 00 0e 10 00 10 2a 01 7e 00 00 00 ..........*.~... 0060 00 00 f0 3c 91 ff fe ae 5f d9 ...<...._.
The interesting part is that you can see the looked up name appearing twice in the human-readable form, but only once in the actual byte stream. To describe why, we need to look at how labels (or names) are stored within the protocol.
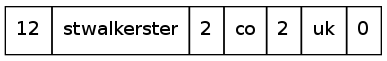
Let's start at a point in the byte stream which is the location of a label. The position I'm gonna look at is byte 0x37, which has the value 0x0c (0d12). This tells us to look for another 12 bytes, which forms this segment of the label. If we read this in, we get "stwalkerster". We now read in the next length byte, which is 0x02 (0d2). This gives us a segment of "co". The next length is also 0x02, which gives us "uk". Finally, we read in the next length (we don't know this is the end yet!), which gives us a length of 0x00, a zero-length label. This is the end of the label.
Thus, the final result is something like this:
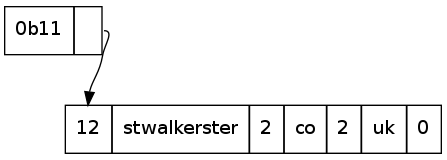
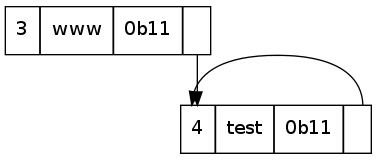
The next instance of this label is at 0x4e. We notice that the first byte has the initial two bits set, so we read the next byte too, to give a value of: 0b1100 0000 0000 1100. The first two bits indicate that this is a pointer, with the rest of the bits indicating the offset from the start of the DNS byte stream the occurrence of the label.
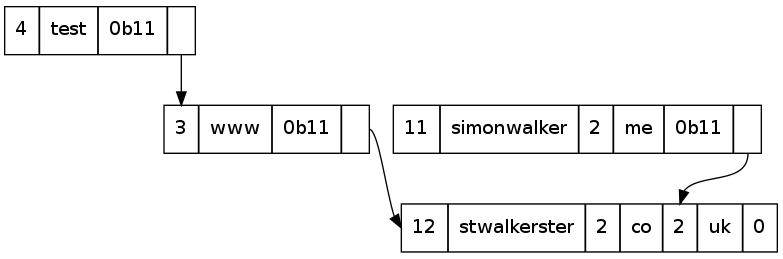
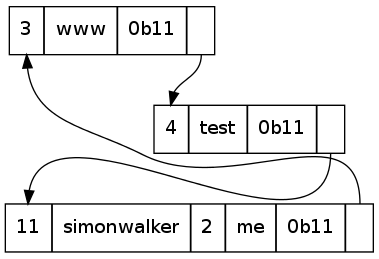
The DNS packet is therefore compressed in such a way that the duplication of the parts of the label already mentioned is eliminated. This is smart, so a packet containing labels for stwalkerster.co.uk, www.stwalkerster.co.uk, test.www.stwalkerster.co.uk, and simonwalker.me.uk will only mention the suffix of a name once:
This pointer-based approach saves a fair amount of bandwidth in large DNS packets where a name may be repeated many times for a round-robin type record.
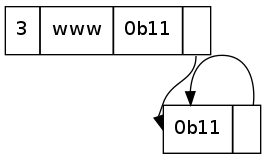
There are some issues with specific implementations of this though, namely the restrictions on where a pointer may point. Consider this:
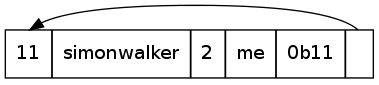
What is the label interpreted by this? simonwalker.me.simonwalker.me.simonwalker.me.simonwalker.me.....
In some bad implementations, this may cause a stack overflow (if done recursively, like mine), or just hang (stuck in an infinite loop, possibly eating RAM). Voila, Denial of Service attack. This can take several forms though, as there could be several pointers involved:
All of the above are technically valid labels. They will just almost never appear as a legitimate request to a DNS server. Any attempt to do something like that should be interpreted as a bad request, or a malicious request and dropped. It shouldn't result in a crash of the DNS server - but I do wonder how many Internet DNS servers are vulnerable to this.